We’re excited to announce that Hello Inbox has acquired clearedin.com, a domain name previously owned by a cybersecurity startup.
While we have acquired the domain, it’s important to clarify that this acquisition pertains solely to the domain name and not the company previously associated with it.
This acquisition presents an excellent opportunity for Hello Inbox to expand it’s email deliverability and security tools to businesses seeking to enhance their email security.
About ClearedIn
ClearedIn offered innovative email security by modeling trusted relationships.
Its patented Identity Trust Graph technology dynamically mapped each organization’s trusted email communication patterns with customers, vendors, and partners.
By continuously learning the hallmarks of legitimate email flows, ClearedIn’s models could identify anomalies signaling account compromise or phishing attacks originating outside the trusted circle.
The platform combined this smart traffic filtering with scanning engines that inspected emails, attachments, and links for malware and credential phishing attempts.
For Microsoft 365 and Google Workspace, ClearedIn integrated directly with Exchange Online and Gmail to secure inbound/outbound mail flows.
Its Zero-Trust Inbox enforced granular access policies based on each user’s trusted graph to block threats before reaching the inbox.
With the Identity Trust Graph’s approach learning organizations’ trusted email sources, ClearedIn eliminated the need for manual whitelisting while providing advanced threat detection and zero-trust email security.
This innovative technology offered seamless protection without the limitations of static block lists.
ClearedIn was acquired in 2022.
About Hello Inbox
Hello Inbox provides a free email deliverability tester, a comprehensive checklist to fix deliverability problems and free tools to generate domain authentication records which are important tools in protecting your business and customers from email spoofing, phishing, and other email-based threats.
Tools to Enhance Email Deliverability & Security
SPF, DKIM, and DMARC are three email authentication protocols that work together to improve email deliverability and security.
Sender Policy Framework (SPF)
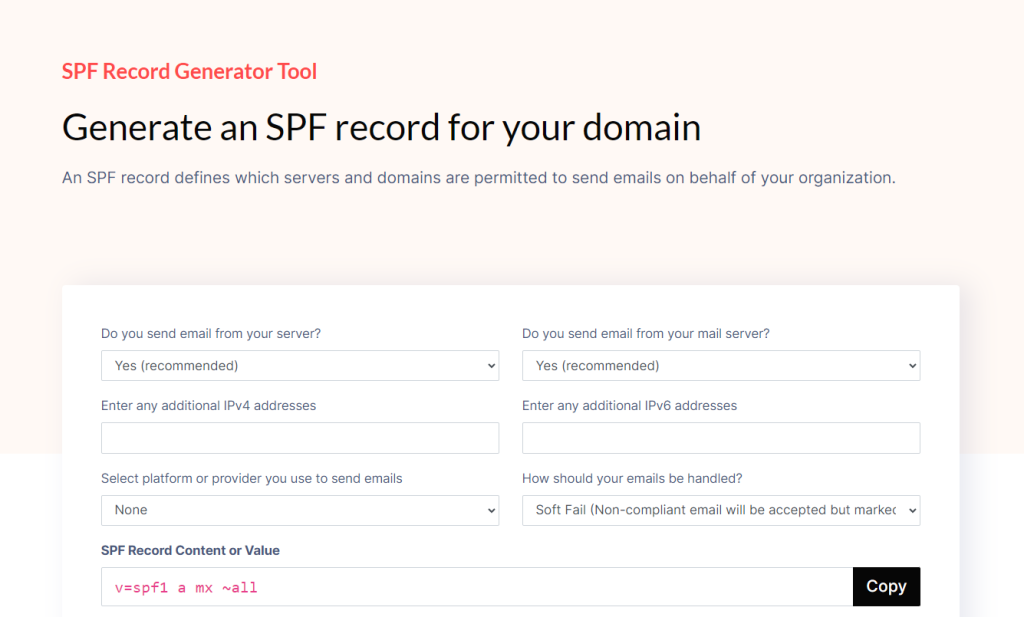
- SPF is a technology that helps to verify the sender’s domain and prevent email spoofing.
- It works by creating a list of authorized sources and IP addresses that are allowed to send emails on behalf of your domain.
- When an email is received, the recipient’s email server can check the SPF record to ensure that the email is coming from a legitimate source.
- This helps to protect your brand from being used in phishing attacks, where cybercriminals might try to impersonate your business to trick recipients into revealing sensitive information or clicking on malicious links.
DomainKeys Identified Mail (DKIM)
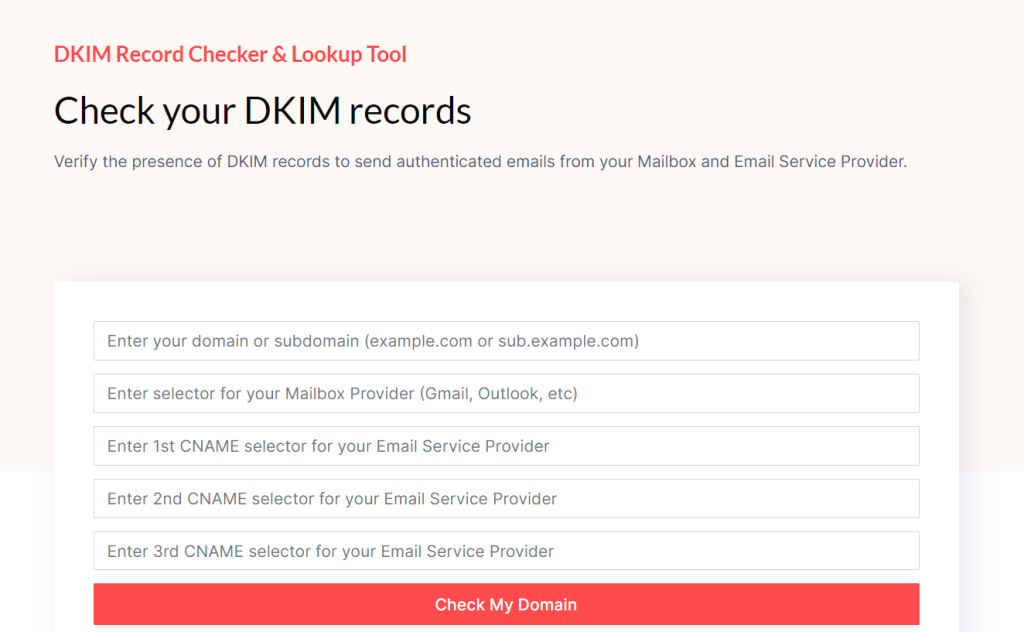
- DKIM is a method of digitally signing emails to verify the authenticity of the sender.
- It adds a digital signature to the email header, which the recipient’s email server can use to verify that the email originated from your domain.
- This helps to prevent email spoofing and ensures that your recipients can trust the emails they receive from your organization.
- DKIM strengthens your brand’s reputation and protects your customers from falling victim to phishing attacks.
Domain-based Message Authentication, Reporting, and Conformance (DMARC)
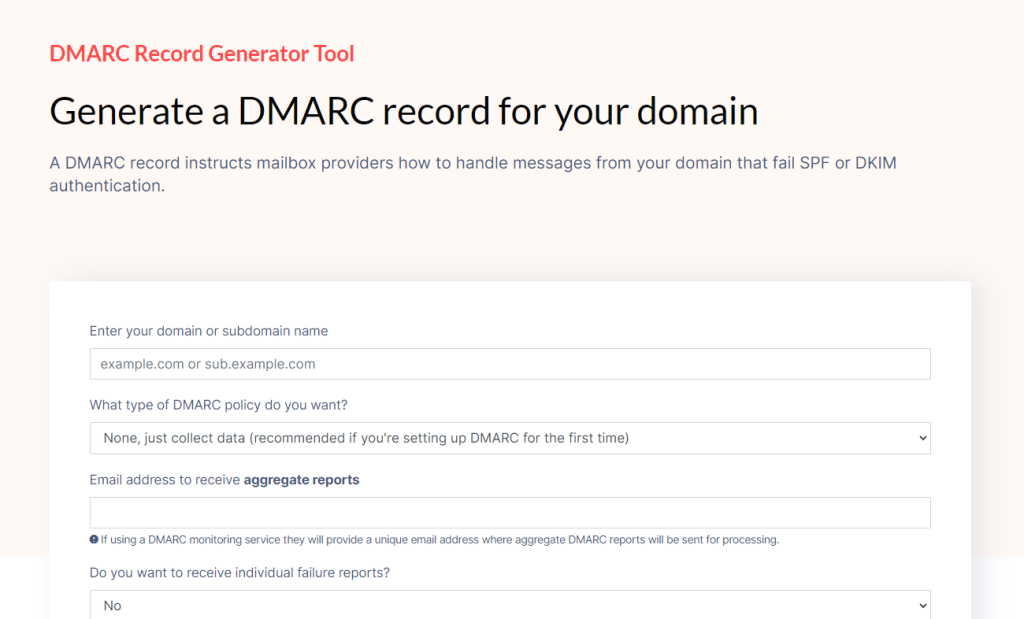
- DMARC builds on the foundations of SPF and DKIM to provide a comprehensive email authentication solution.
- DMARC allows you to specify how your domain should handle emails that fail SPF or DKIM checks.
- It provides reporting capabilities, allowing you to monitor and analyze the email traffic to your domain, including any attempts to spoof your brand.
- DMARC helps to protect your brand by ensuring that only legitimate emails are delivered, and it provides valuable insights into potential security threats.
By implementing these domain authentication protocols, you can greatly reduce the risk of phishing attacks targeting your business and your customers.
It also helps to maintain a strong sender reputation, which is crucial for the successful delivery and inbox placement of your email communications.
Implementing SPF, DKIM, and DMARC demonstrates your commitment to email security and your customers’ trust.
It’s a proactive step towards safeguarding your brand and protecting your recipients from the dangers of email-based threats.
Email security related articles
- Biggest Data Breaches of all Time from Email Phishing
- Reasons Why Spear Phishing Attacks Are Successful
- 10 Eye-Opening Phishing Attack Statistics
- DMARC Compliance Explained
- Typical DMARC Compliance Process: Step-by-Step Guide
